


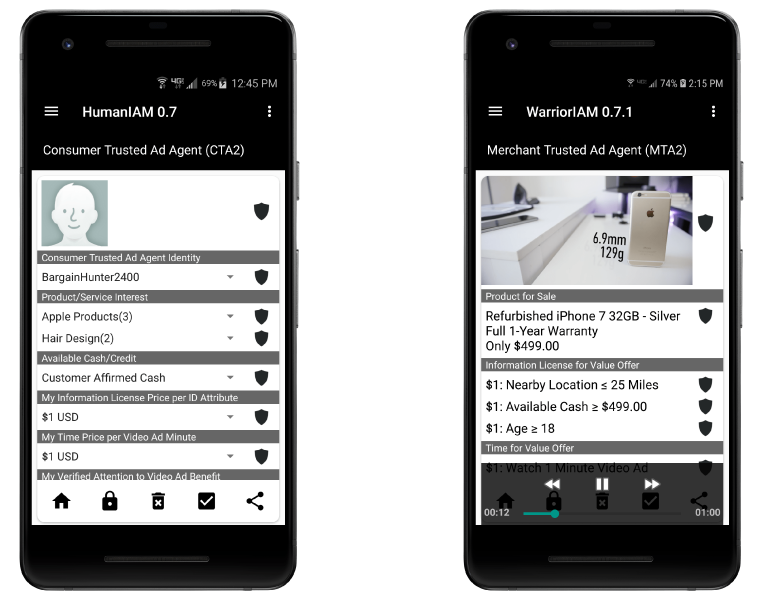
Provides the capability to manage secure, trustworthy and privacy respectful electronic commmerce and advertising communities. Prototype Consumer Trusted Ad Agent™(CTA™) and Merchant Trusted Ad Agent™(MTA™) are designed to support direct (agent to agent) relationships between consumers and merchants.
If merchants want a piece of our data, time and attention to their ads, they need to pay us. They need to talk to our agent, our Personal Information Agent.
Never sell your information, license it and always maintain control.
Distinct advantages for merchants are that these agent (CTA2) to agent (MTA2) relationships are direct, trustworthy - privacy and security respectful, highly adaptable, precisely focused and provide immediate feedback on what works and does not.
CYVA's agent-based information-for-value and/or benefit ads are B2C market driven, not set by ad agencies or the search or mobile ad firms.
As shown merchants can include video clips and negotiate terms directly with their customers.
Watch Prototype Video Learn More
Provides the capability to establish and manage secure, privacy respectful, trustworthy, PIA-based communities. eMetro™ operators can resell Personal Information Agent™ (PIA™) licenses, set up and manage PIA-based communities for their community member clients.
Watch Prototype Video
Capabilities include providing humans continuous protection and control over their deployed digital identities and information assets wherever they exist across hostile environments; and the formation and management of Trust Communities (TCs). The HumanIAM platform and services augment humans amplifying their abilities for security, privacy and liberty.
Watch Prototype Video
Capabilities include continuous protection and control over the warrior deployed digital identities and information assets wherever they exist across hostile environments; the formation and management of ad hoc compartmental smartphone-based Trust Communities (TCs) supporting intelligence, surveillance, and reconnaissance (ISR) operations.
Warriors directly control, that is, lock at will, audit at will, change governing security policies (actions permitted, identity agent privileges, community based privileges, metered time,...) at will, erase at will their deployed identity agents and information assets (target data, pictures, messages,…) post-decryption, wherever their agents exist.
Watch Prototype Video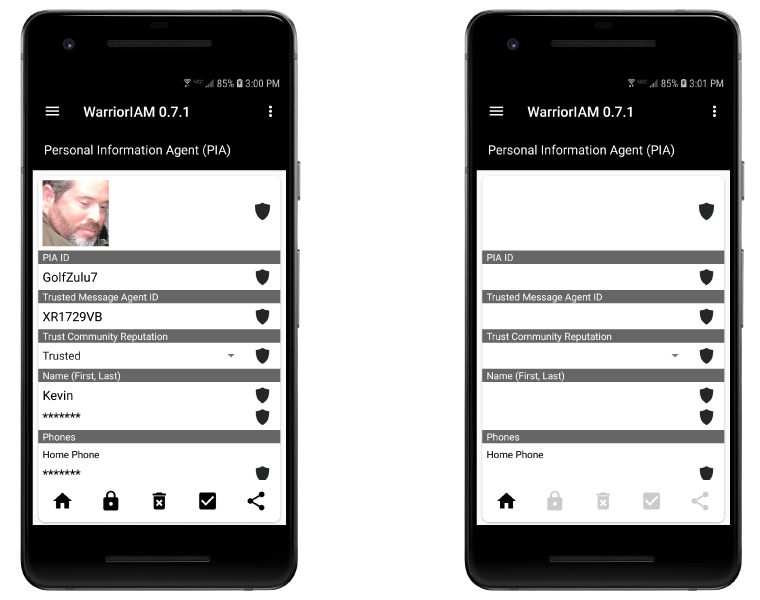
CYVA's PIA Communicator™ is a smartphone application that manages the owner-operators PIAs, guest PIAs and IoT device PIAs. The owner-operator authors, maintaines and deploys and communicates with their deployed PIAs, EMAs, CTA2, MTA2 and other agents.
The PIA Communicator™ supports PIA to PIA communications. In the image capture above the PIA owner-operator is erasing one of their deployed PIAs, exercising their right to be forgotten.
Watch Prototype Video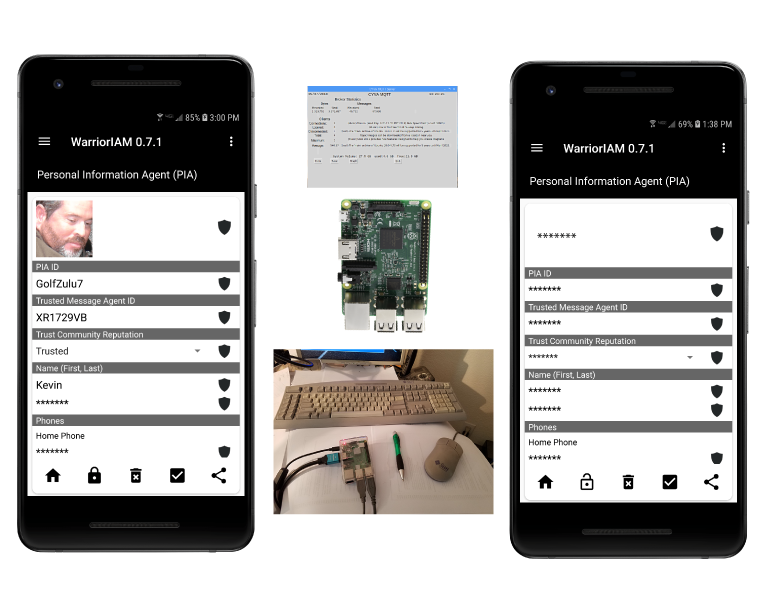
Provides Trust Community (TC) operators a high survivability, secure, small form factor, portable kit to independently operate and manage their own TCs, support PIA to PIA communications and resell PIA licenses.
Watch Prototype Video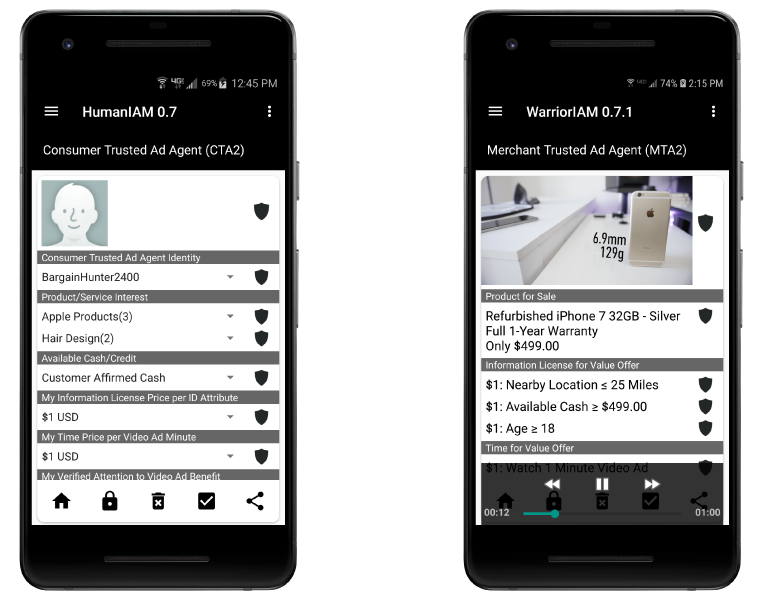
PIB2 platforms and services represent a much-needed change in who owns, controls, and profits from our personal information assets. It is time to disrupt the out-of-control collection and exploitation of our personal information and put people in direct, authoritative control of their information assets wherever they exist.
PIA owner-operators set their own pricing (monetary and/or discounts) for the trustworthy use of their information assets; and also, be fairly compensated for their time and attention to merchant advertisements. Merchants make information-for-value and/or benefit offers to individuals or groups. This helps foster a free market of willing parties engaged in commerce that benefits from the secure, privacy and liberty respectful use of personal information assets.
We recommend individuals never sell their personal information but license it and always maintain direct, authoritative control over their identity and information assets.
We wish to restore trust between merchants and consumers and recognize the value to our digital culture and economy of respecting Human Digital Dignity, Human Digital Integrity, Human Digital Liberty. We have mutual rights and responsibilities to protect ourselves, one another and to disrupt and halt as much as possible the out-of-control collection and exploitation of our human digital existence, our personal information.
We propose a new industry: Personal Information Banking and Brokerage™, wherein people individually and/or in groups set the pricing, terms and conditions for the trustworthy use of their data, their time and attention to ads and other types marketing messages.
Watch Prototype Video
What goes around comes around (WGACA), the good and the bad. WGACA.COM is a reputation management system that is designed to be secure, privacy respectful, trustworthy and facts based. It is difficult these days to know what is true and factual on the internet as so much information is disinformation, false and purposely misleading.
A WGACA File™ is a means for the folks to provide their honest opinions about others and/or their products and services, the good and the bad as they see it and back up their WGACA reputation claims with facts, with evidence and not add to the deceitful practices of those who simply want to destroy others, rather than building them up.
We all have a responsibility to maintain the integrity of the chain of command and especially hold accountable those in high office or positions of power. Double honor for those who rule well, who uphold justice for all under the law, no favoritism, no corrupt self-dealing. WGACA is also a means to praise those who serve well and give them the due honor their actions, their deeds deserve. High praise.
Watch Prototype Video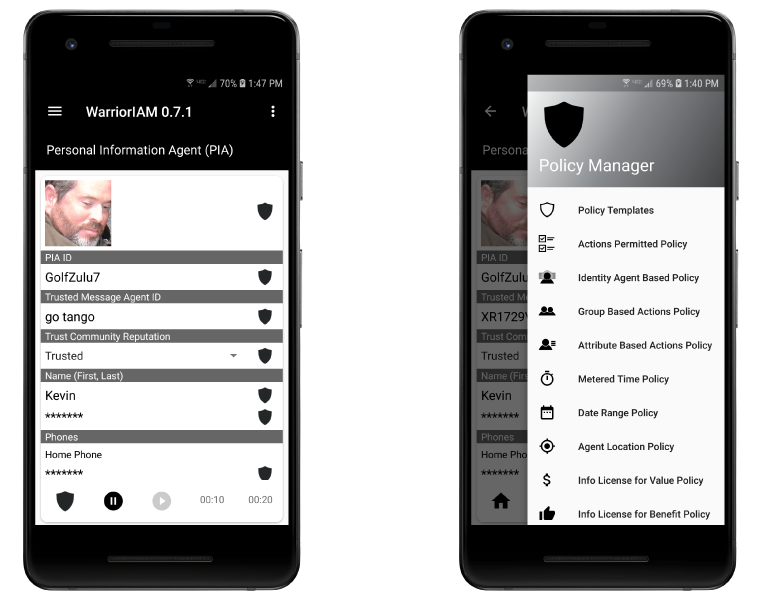
Provides an individual the capability to protect and control their agent-based digital identity and information assets wherever they exist.
PIA owner-operators author their own security, privacy and liberty policies. These policies are bound/assigned to their identity and information assets and travel with them, always-on, always enforcing their security, privacy and liberty rules: Human Digital Integrity principle.
As an example a PIA owner-operator can set a Metered Time policy wherein there is a limited amount of time, say 30 seconds that a PIA recipient can display or see the displayed PIA. A person might send a picture or a message that is contained within their PIA and limit the display time to 1 minute or 24 hours. The Metered Time policy can be dynamically set by the PIA owner-operator.
Metered Time policy is one of currently 18 policy types or categories of security, privacy and liberty rules being developed.
We are augmenting humans, amplifying their ability to protect and control their information wherever it exists; and enforce their rights and encourage their mutual responsibilities for security, privacy and liberty for all.
Watch Prototype Video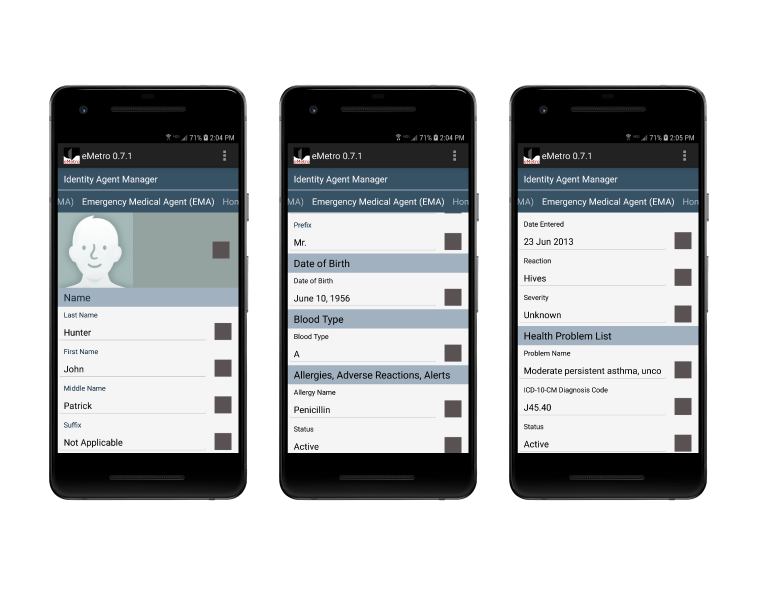
CYVA's EMA™ is a patient-controlled emergency medical identity that is designed to securely place the right information in the hands of the right people at the right time. The EMA™ provides patients and/or their chosen custodians direct, continuous control over their agent-based emergency medical information wherever it exits.
Today medical identity theft is out of control. It is far too common that criminals gain unauthorized access to our weak, primitive, easy prey data. And with the explosion of Ransomware attacks, encryption technology is being used against us and the healthcare organizations responsible to protect our medical records.
Shown above is an early EMA prototype containing essential emergency medical information. Our proposal is to provide individuals and their chosen physicians (healthcare providers) the capability to place this critical emergency medical information (blood type, allergies, adverse reactions, alerts, health problem list, medications, physical characteristics, patient ID picture, and more) within in a patient-controlled Emergency Medical Agent™ that is continuously under the direct control of the patient and/or chosen custodian wherever it exists.
Patients can lock at will, audit at will, dynamically set security, privacy and liberty policy at will and erase at will (right to be forgotten). A use case is when an emergency occurs, patients and/or their chosen custodians can dispatch their EMA to a chosen emergency community and maintain direct control of the use our their EMA-based medical information.
Watch Prototype Video
These are consumer and merchant controlled and prospered mobile advertising services that are designed to build and enforce trustworthy, security and privacy respectful relationships between merchants and consumers.
Consumers, according to their terms and conditions derive value (monetize) and/or benefit (discounts) from the trustworthy use of their information.
Social media, mobile advertising, search engine and other tech giants make billions off our personal information.
I believe it is time for change. It is time to take control of the collection and monetization of our personal information assets.
If merchants want a piece of our data, time and attention to their ads, they need to pay us. They need to talk to our agent, our Personal Information Agent.
Never sell your information, license it and always maintain control.
Distinct advantages for merchants are that these agent (CTA2) to agent (MTA2) relationships are direct, trustworthy - privacy and security respectful, highly adaptable, precisely focused and provide immediate feedback on what works and does not.
These agent-based information-for-value and/or benefit ads are B2C market driven, not set by ad agencies or the search or mobile ad firms.
As shown merchants can include video clips and negotiate terms directly with their customers.
Watch Prototype Video