



CYVA Research is a cybersecurity innovation, strategic research and development firm. Our focus is developing disruptive security, privacy and liberty technologies and strategies for our clients.
CYVA's internationally patented Personal Information Agent™ (PIA™) technology is an owner-operator controlled, intelligent (Safe White Box AI™), self-protecting, self-governing, self-monetizing mobile identity agent (HW/SW). The PIA™ provides, augments people and communities with the capabilities to own, protect, control and license-monetize their identity and information assets wherever they exist post-decryption. These capabilities are the foundation in forwarding disruptive innovative approaches to the challenges of security, privacy and liberty in our presently hostile cyberspace.
Our mission is to provide people the capabilities to own, protect, control and license (monetize) their personal information assets wherever they exist according to their terms and conditions. We encourge people to never sell their personal information but to license and continuously control their information assets wherever they exist.
We call this Human Digital Liberty™.
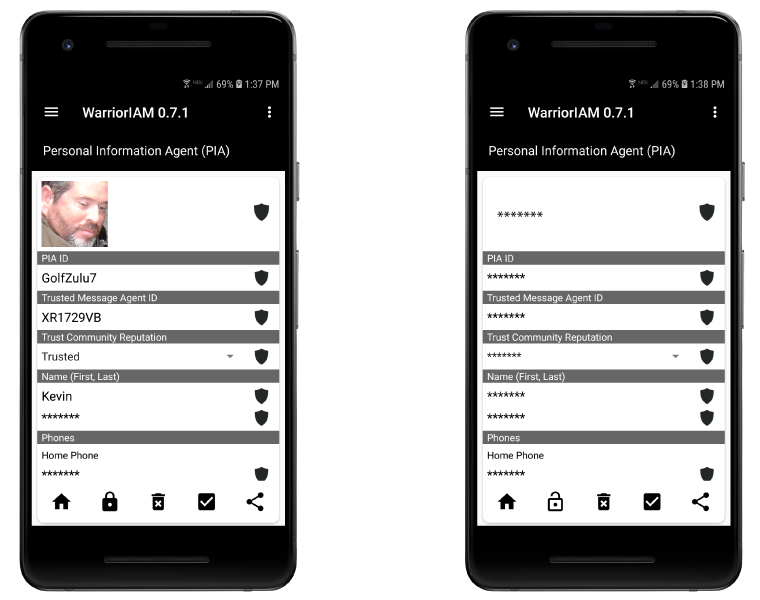
Lock/Unlock your PIA™, your PIA-based personal information anytime, anywhere. Enforce your right to control your personal information wherever it exists.
Watch Prototype Video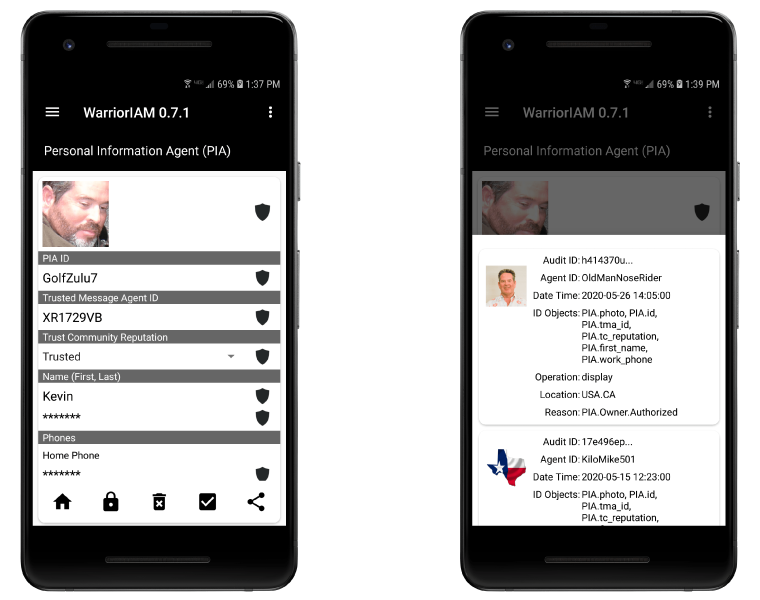
Audit the use of your PIA-based identity and information assets. Know the who, what, where, when and why of any use of your personal information (medical, location, pictures, identity attributes).
Watch Prototype Video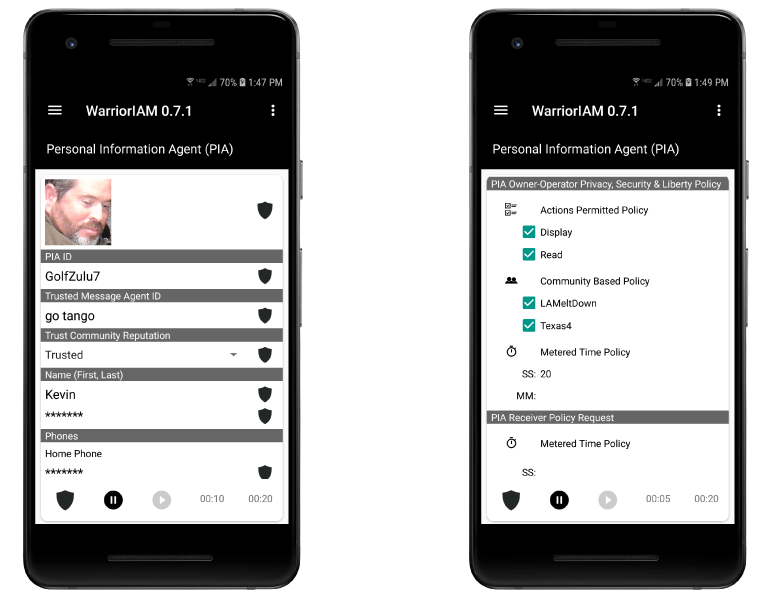
At your discretion, change your governing privacy, security and liberty policies. In this example the PIA owner-operator is setting their Metered Time policy to 20 seconds. After the 20 seconds countdown completes the PIA erases. Optionally, the PIA recipient can request more time.
Watch Prototype Video
Erase your PIA-based personal information anytime, anywhere. Enforce your right to control your personal information wherever it exists.
Watch Prototype Video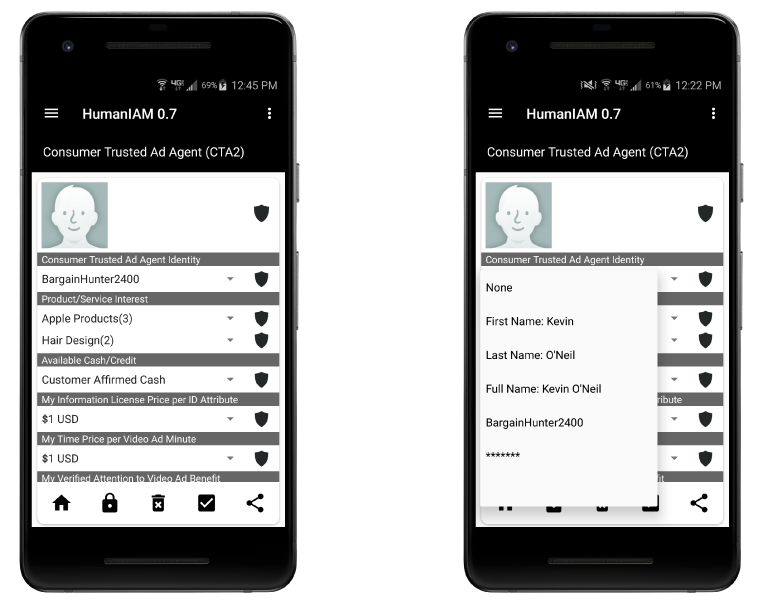
Control exactly what about yourself do you wish to make available. Do you want to be anonymous and use your own chosen nickname or a handle such as BargainHunter2400 for this situation? You decide your level of identity precision: anonymous, pseudonymous or fully identified. You decide which identity is appropriate given your concerns, your choices for privacy, security and liberty.
Watch Prototype Video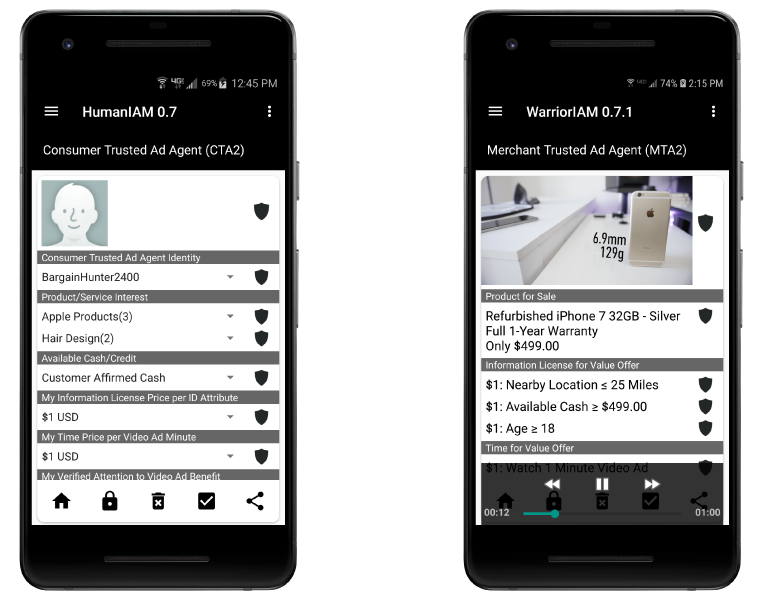
According to your terms and conditions derive value (monetize) and/or benefit (discounts) from the trustworthy use of your information.
Social media, mobile advertising, search engine and other tech giants make billions off our personal information.
I believe it is time for change. It is time to take control of the collection and monetization of our personal information assets.
If merchants want a piece of our data, time and attention to their ads, they need to pay us. They need to talk to our agent, our Personal Information Agent.
Never sell your information, license it and always maintain control.
Distinct advantages for merchants are that these agent (CTA2) to agent (MTA2) relationships are direct, trustworthy - privacy and security respectful, highly adaptable, precisely focused and provide immediate feedback on what works and does not.
These agent-based information-for-value and/or benefit ads are B2C market driven, not set by ad agencies or the search or mobile ad firms.
As shown merchants can include video clips and negotiate terms directly with their customers.
Watch Prototype Video
Owner-Operator Controlled, Intelligent (Safe White Box AI™), Self-Protecting, Self-Governing, Self-Monetizing Mobile Identity Agent.
Today our information is weak, vulnerable, easy prey. This is by design.
Big Tech promotes and maintains a weak-primitive data paradigm as it serves their goals of maximum profits and control.
What if data was re-engineered, designed to be under our control (post-decryption), self-protecting, self-governing?
For 85 years U.S. auto manufactures built cars without safety belts. Thousands died. The government had to force manufactures to make safety belts standard equipment.
Today there is no end in sight to cybercrime, cyber terrorism. Our data has no safety belts.
As a result of this willful negligence, millions of people are being harmed (identity theft, credit card fraud, medical identity theft, stalking, harassment,...) and businesses losing billions. And these are some of the consequences of weak, vulnerable, easy prey data objects that were never designed to be under our control, self-protecting, self-governing.
Security Rule #1: Trust no one. Especially do not trust any individual or organization that does not respect our right to protect and directly control our personal information wherever it exits.
Owner-Operator Controlled Digital Identity: Your Personal Information Agent (PIA) enforces your right of informational self-determination, your right to control your information wherever it exists.
Privacy is not an absolute right. The right of an individual to control their personal information, the information regarding you as a person has limits. Context: the who, what, where, when and why and guiding principles of equal justice under law, due process, sanctity of life, historical judicial opinions, enterprise architecture, software and system frameworks, systems engineering models, domain taxonomies, data dictionaries and enforcement technologies and systems are essential to understanding, describing and addressing privacy (informational self-determination), data protection rights and responsibilities.
There exists an abundance of privacy principles defined and enumerated in various documents such as the OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data, General Data Protection Regulation (GDPR), GDPR Right to be Forgotten, California Consumer Privacy Act (CCPA), HIPAA Privacy Rule, and others as we grapple to address what to do about security, privacy and liberty.
Today there is a massive imbalance and inequity of power over who owns and controls our personal information.
We are augmenting humans, amplifying our abilities to protect and control our personal information, our human digital existence. We are equipping liberty minded people worldwide to fight against tyrants, those who do not respect our unalienable rights, our foundational values and principles declared in our U.S. Constitution.
Tyrants have long engaged in spying on their citizens, conducting unlawful surveillance, censorship, intimidation, persecution, and oppression. Today crony Big Tech and corrupt Big Governments (.e.g., the swamp, the communists, the facists) want a weak, vulnerable, easy prey population that they can enslave, exploit, manipulate, control and slaughter at will.
Is is essential to liberty that we, the people, be equiped to fight for liberty in a hostile and rigged cyber world, to do what is right (ethics-driven) and mutually respect our shared Human Digital Dignity, our shared rights and responsibilities to protect one another, to respect the sanctity of all human life.
If you value your security and liberty never surrender your rights, your capability to protect and control your personal information wherever it exists. People are beginning to realize the lie, the false trade-off in giving up privacy for security.
We have long known the necessity of self-protection in a hostile physical world, the right to bear arms, to be secure in our person, home, papers and effects. Cyberspace is no exception. And presently, our information is weak, vulnerable, easy prey. This is by design.
Information can be used for us (good) and against us (evil). It is critical to understand and know as fact, that our present human digital existence, our personal information is largely out of our control. We are purposely denied authoritative direct control over our personal information, and therefore are perilously unable to prevent having our information used against us (evil). This is by design.
We are all subject to always-on surveillance. Companies are tracking our location, recording our behavior in an expanding network of smartphones, cars, homes, appliances, TVs, AI face recognition capable video camera systems. Our environment, public and private, is systematically being infused with spytech.
Super profiles have and continue to be built and shared across a sea of data brokers, our modern day data slave traders/human digital traffickers who profit from our personal information in advertising schemes, making billions in revenue, while negligently exposing us all to a never ending onslaught of cyber crime and cyber terrorism.
Crony Big Tech and corrupt Big Government maintain this status-quo of maximum control by themselves over our personal information. This is by design.


There has been a war raging for years over who owns and controls personal information and we are the losers. By design, our personal information is weak, vulnerable, easy prey.
Crony Big Tech and corrupt Big Government have and continue to work together to maintain the status quo: a business model and strategy of maximum control and exploitation of personal information.
CYVA Research argues for the re-engineering, the redesign of primitive data objects, our compute fabric at an atomic level, creating a new class of owner-operator controlled, self-protecting, self-governing mobile information objects.
This new class of owner-operator controlled, self-protecting, self-governing objects (HW/SW) are designed to augment humans, providing us the capabilities to protect and control our digital identity and information assets wherever they exist.
CYVA's Self-Determining Digital Persona is built according the firm's guiding architecture principles: Human Digital Dignity™, Human Digital Integrity™, Human Digital Liberty™.
We believe in unalienable human rights and the mutual responsibility to respect and protect those rights in both the physical world and digital world: cyberspace.
Today, we are realizing that we are Human Digital Persons, people with a digital existence. Our unalienable rights to life, liberty and prosperity are under assault in this manmade catastrophe called cyberspace, that, by design, is hostile to security, privacy, and liberty.
I believe there are millions of people today who now realize just how precarious our digital existence is, how vulnerable we all are in this rigged-for-enslavement, rigged-for-tyranny world called cyberspace, and are motivated to act, to fight for their Human Digital Liberty.
It is essential to understand that the unending and escalating cybersecurity catastrophe we are experiencing is entirely manmade.
Presently there is no end in sight to data breaches, cybercrime, and cyber-attacks by criminals and our enemies.
Target (November 2013, 145 million records),
Yahoo (2013 3 billion records, not determined until 2017),
eBay (2014 145 million records)
JP Morgan Chase (2014, 83 million records),
Anthem (2015, 80 million records),
United States Office of Personnel Management (OPM) (2014-2015, 21.5 million highly sensitive SF 86 files)
Myspace (May 2016, 360 million records),
LinkedIn (May 2016, 100 million records),
Equifax (2017, 143 million records),
Uber (October 2016 57 million records, concealed from regulators until November 2017).
Data Records Lost or Stolen Since 2013 (Global) 9,727,967,988.
Records breached in the Year 2017 (Global) 2,600,968,280.

With the advent of cyberspace as an operational domain of war, criminals and our enemies have skillfully exploited our present weak, vulnerable, easy prey state of being digital.
Special Operations Forces (SOF) and their families have and continue to be hunted online. They are priority targets for our enemies.
All of us are being surveilled online, profiles being built and shared across a sea of players who expose us to harm.
Presently, civilians and warriors have little if any control over their human digital existence, their digital identity and information assets.
This includes Social Security numbers, cellphone numbers, home and work addresses, e-mail addresses, IP addresses, photos, real-time location data, names of spouses and children, text messages, chat, web searches, blood type, medications, biometrics, finger prints, facial scans, videos.

Core to our manmade cybersecurity catastrophe is the fact that primitive data types (data objects) were never designed to be secure, to be self-protecting, self-governing.
Common primitive data types include:
integers (62, 1000, -37)
booleans ('true' 'false')
characters ('x' '$' '2')
floating-point numbers (21.003, -500.89)
alphanumeric strings (‘today is Friday’).
Primitive data types (data objects) and file formats such as JASON and XML files, these basic, atomic building blocks of information systems cannot protect or govern themselves. This is by design.
In other words, the Data Object is the most fundamental flaw in our critical information technology fabric. As a result, our information is weak, vulnerable, easy prey.
This is a fundamental flaw and continues to put us all at risk and in particular Special Operations Forces (SOF) Warriors and their families who are being hunted by our adversaries.
Encryption is valuable, but we need to go beyond encryption.
Encrypting primitive data is not enough as the explosion in Ransomware has demonstrated: encryption being used against us.
Encrypted message:
0DD8CC1D95853D9F6CF9149810EE100C267881337E66199682B8BB19A410D87ECA3AE298F64B62AD7C3457FF3C1E10A9
If you encrypt a data file, share that encrypted file and later provide the recipient the decryption key, do you have any control over the decrypted file?
No. You have zero control.
Plain Text: "Meet me at location jubilee at 1300 hours."
The recipient can do whatever they want (operations: read, update, send) with the decrypted data. We need to go beyond encryption as its purpose is to hide/distort the meaning of, scramble data, not Control the Operations performed on the data.
Our approach of self-protecting mobile information objects combines the ‘scramble data’ utility of encryption with an individual's ever protecting, and present rules of information access and use; you control the processing as your processing rules are always present. Note these are your rules not some unknown administrator or business/government entity that says you have to trust us.
So after an encapsulated agent-based information object is decrypted the owner-operator (you) remains in operational control (read, display, update, exchange, delete, lock down,…) of the information. An individual can change a governing policy or remotely lock-down any deployed Personal Information Agents at will (see prototype demo video). Security rules are pre-set and can operate autonomously or semi-autonomously.
CYVA Research has designed a new class of self-protecting, self-governing mobile information objects, a Self-Determining Digital Persona™ that enforces privacy and empowers the right of people to be secure and free in their human-digital existence. These technologies are being built in accordance with our guiding architecture principles: Human Digital Dignity™, Human Digital Integrity™, Human Digital Liberty™.
We all should respect Human Digital Dignity™ - we have a human digital existence and the right of informational self-determination - Human Digital Liberty™, the right of people to be secure in their human-digital existence and the liberty to control and derive value and/or benefit from the trustworthy use of their digital identity and information assets according to their terms and conditions. It is a fundamental design objective to build systems that support and affirm Human Digital Dignity and the rights-responsibilities of privacy: informational self-determination.
Human Digital Integrity™: never separate a person’s data from their policies, and the capability for a person or authorized custodian to enforce governance over the use of their Human Digital Identity wherever they exist.
Today we artificially separate policy from data. Our design, our architectural principle is to never separate a person’s rules, their security and privacy choices from their data; a person’s rules, their policy travels with their data.
Consumer privacy and security rules, and auditing are always on, always enforcing consumer privacy-security choices, recording the who, what, where, when, why details of data processing. This capability provides data controllers a verifiable means to prove and satisfy certain long standing data protection principles and evolving data protection regulations (e.g., General Data Protection Regulation (GDPR), OECD Privacy Guidelines, HIPAA/HITECH, California Consumer Privacy Act (CCPA)).
Ralph Nader confronted the auto industry in 1965.
"Unsafe at Any Speed: The Designed-In Dangers of The American Automobile"

For approximately 85 years automobile safety belts were not standard equipment.
Nader claimed American automobiles were generally unsafe to operate. Unsafe at Any Speed became an "immediate bestseller but also prompted a vicious backlash from General Motors (GM) who attempted to discredit Nader".
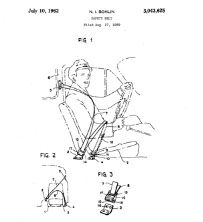
In 1966, Congress passed the National Traffic and Motor Vehicle Safety Act - seat belts being required on all new American vehicles from 1968 onward.
Our data has no safety belts.
Our data has no capability to self-protect, to self-govern and certainly no capability for you and me to directly control (e.g., lock, unlock, erase forever, derive value/benefit as we determine) our personal information anywhere, anytime.
This is by design.
Data is collected and used for one purpose and later used for a completely different purpose.
Einsatzgruppen (Nazi Death Squads) can be traced back to the ad-hoc Einsatzkommando formed by Reinhard Heydrich to secure government buildings and documents...1938.
The task of securing government buildings with their accompanying documentation and the questioning of senior civil servants in lands occupied by Germany was the Einsatzgruppen's original mission.
The Nazis prepared a detailed list identifying more than 61,000 Polish targets (mostly civilian) by name.

Special Prosecution Book - Poland
In 2013, the United States Internal Revenue Service (IRS) revealed that it had selected political groups applying for tax-exempt status for intensive scrutiny based on their names or political themes.
May 2010...began developing a spreadsheet that became known as the "Be On the Look Out" ("BOLO") list.
You and I have little if any direct control over the repurposing of the vast and growing amount of data collected (electronic records) about us.
This is by design.
Our industry is stuck in and perpetuates a primitive, weak, easy prey data paradigm.
We are blinded and constrained by this idea of protecting an object that was never designed to protect itself, that was never designed to govern itself.
Perpetuating primitive, weak, easy prey data is essential to the status quo and a business model and strategy of maximum control and exploitation of personal information by crony big business (greed-driven) and corrupt big government (power-driven).
Especially do not trust any individual or organization that does not respect and protect our human right to control our personal information wherever it exists.
Data can be used for us (good) and against us (evil).
Today our data is weak, vulnerable, easy prey.
This is by design.
The human right of privacy: informational self-determination is not an absolute right. Our right to control our personal information is essential to security, privacy and liberty, but it is not an absolute right, namely it is not true in all situations.
Example: Criminal Record
"When someone is convicted of a crime in a United States courtroom, it is a public event. The record of the conviction is a public record, and anyone can go to a court clerk's office and search the files for records of conviction for a certain person" (exception: judge sealed, expunged conviction).
Source: nolo.com
Why fight those who believe and behave like the Nazis, the Transatlantic slave traders and tyrants who sought to enslave, subjugate and annihilate people they asserted were sub-human, not worthy of life and liberty?
I believe there are millions of people today who now realize just how precarious our digital existence is, how vulnerable we all are in this rigged-for-enslavement, rigged-for-tyranny world called cyberspace, and are motived to act.
Like those who fought evil in the past, they will fight to secure Human Digital Liberty for themselves and others they love and cherish.
Consider, the only rights you have are those you fight for.
Warrior I am.
Take control of your personal information, abolish the Data Slave Trade and the Anti-Liberty Surveillance State.
Secure the benefits of Human Digital Liberty, your right to protect and control your personal information wherever it exists; and derive value and/or benefit from the trustworthy use of your information assets in accordance to your directly enforceable terms and conditions.
There has been a war raging for years over who owns and controls personal information and we are the losers. By design, our personal information is weak, vulnerable, easy prey.
Crony Big Tech and corrupt Big Government have and continue to work together to maintain the status quo: a business model and strategy of maximum control and exploitation of personal information.
CYVA Research argues for the re-engineering, the redesign of primitive data objects, our compute fabric at an atomic level, creating a new class of owner-operator controlled, self-protecting, self-governing mobile information objects.
This new class of owner-operator controlled, self-protecting, self-governing objects (HW/SW) are designed to augment humans, providing us the capabilities to protect and control our digital identity and information assets wherever they exist.
CYVA's Self-Determining Digital Persona is built according the firm's guiding architecture principles: Human Digital Dignity™, Human Digital Integrity™, Human Digital Liberty™.
We believe in unalienable human rights and the mutual responsibility to respect and protect those rights in both the physical world and digital world: cyberspace.
Today, we are realizing that we are Human Digital Persons, people with a digital existence. Our unalienable rights to life, liberty and prosperity are under assault in this manmade catastrophe called cyberspace, that, by design, is hostile to security, privacy, and liberty.
I believe there are millions of people today who now realize just how precarious our digital existence is, how vulnerable we all are in this rigged-for-enslavement, rigged-for-tyranny world called cyberspace, and are motivated to act, to fight for their Human Digital Liberty.
If you value your liberty never surrender your rights to protect and control your personal information wherever it exists. People are beginning to realize the lie, the false tradeoff in giving up privacy for security.
We have long known the neccesity of self-protection in a hostile physical world, the right to bear arms, to be secure in our person, home, papers and effects. Cyberspace is no exception. And presently, our information is weak, vulnerable, easy prey. This is by design.
Information can be used for us (good) and against us (evil). It is critical to understand and know that our present human digital existence, our personal information is largely out of our control. We are purposely denied authoritative direct control over our personal information, and therefore are perilously unable to prevent having our information used against us (evil). This is by design.
We are all subject to always-on surveillance, tracking our location, recording our behavior in an expanding network of smartphones, cars, homes, appliances and offices filled with embedded IoT devices and spyware. Super profiles have and continue to be built and shared across a sea of data brokers, our modern day data slave traders/human digital traffickers who profit from our personal information in advertising schemes, making billions in revenue, while negligently exposing us all to cyber criminals and cyber terrorist.
Crony Big Tech and corrupt Big Gov maintain this status-quo of maximum control by themselves over our personal information. This is by design.
We all have a human physical and spiritual existence, and now a digital existence. I believe human beings were created in God's image and as image bearers we have a sacred God given dignity. Life is sacred, life is precious. Life is to be valued, respected and protected.
Today we have a human digital existence that bears our likeness and therefore is also sacred, precious, to be valued, respected and protected.
However, our human digital person like so many people in our past and present have suffered, and are suffering a new kind of indignity, a humiliation. Our human digital person, our personal information is being captured, chained, branded, declared property and put to work, a new kind of slavery – human digital slavery.
CYVA is building, architecting a new kind of data object (SW/HW) that protects and enforces respect for our human digital person, our human digital dignity.
Never seperate a person's data, their personal information from their security, privacy and liberty rules, their policies, terms and conditions governing any collection or use of the person's human digital person, their information.
A person's governing choices, their policy detailing who, what, where, when and why should anyone and/or thing (machine: IoT device) be able to collect and use that individual's personal information should not be seperated from their data, their information assets.
These rules should be assigned to and bound to our personal information objects (pictures, identity details, medical information, financial information, location information, our messages,...) traveling with our data, always protecting, always enforcing our rules, our security, privacy and liberty choices.
It is our design to maintain and protect the bodily integrity of our human digital person, assign and bind our personally chosen governing policies, our security, privacy and liberty rules to our data. This design is to disrupt human digital trafficking, to help protect us from the violence of those who steal our data, who kidnap our human digital person for profit and power.